Global Law Enforcement Collaboration Takes Down ‘LabHost’ Phishing-As-A-Service Platform
The Takedown of the LabHost Platform is a Major Step in Reducing Phishing Scams
Authors:
• SCARS Editorial Team – Society of Citizens Against Relationship Scams Inc.
• Portions from Europol and UK Metropolitan Police
About This Article
Law enforcement agencies from 19 countries collaborated in a year-long operation to disrupt ‘LabHost,’ one of the world’s largest phishing-as-a-service platforms. Coordinated by Europol, the operation resulted in the compromise of LabHost’s infrastructure and the initial arrest of 37 suspects, with the potential for as many as 1,000 more arrests.
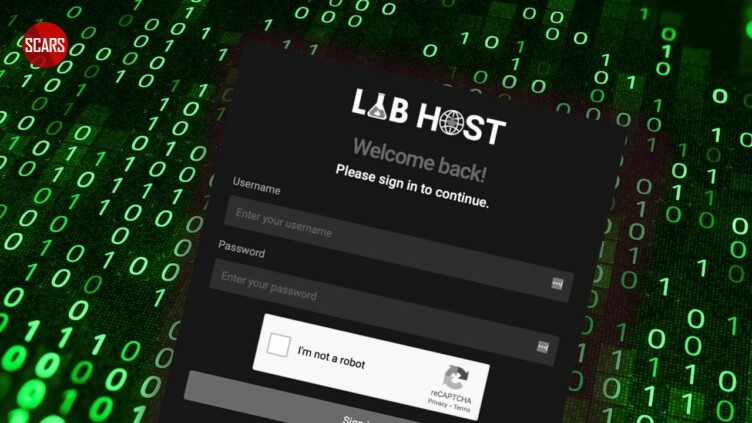
LabHost facilitated phishing attacks on users of hundreds of financial institutions worldwide for a monthly subscription fee. The platform, previously available on the open web, has been shut down following the investigation.
Led by the UK’s London Metropolitan Police, with support from Europol and other agencies, the investigation uncovered over 40,000 phishing domains linked to LabHost and identified approximately 10,000 users worldwide. This international effort underscores the seriousness with which law enforcement agencies are combatting cybercrime on a global scale.

Law Enforcement from 19 Countries Severely Disrupted one of the world’s largest Phishing-as-a-service platforms known as ‘LabHost’
This year-long operation, coordinated at the international level by Europol, resulted in the compromise of LabHost’s infrastructure.
International investigation disrupts phishing-as-a-service platform LabHost
Dozens were arrested initially – 37 in total, but it is believed that it will lead to the arrest of as many as 1,000 or more!
Facilitating Phishing Scams
LabHost facilitated the phishing of users of hundreds of financial institutions worldwide for a monthly subscription fee
Between Sunday 14 April and Wednesday 17 April 2024, a total of 70 addresses were searched across the world, resulting in the arrest of 37 suspects. This includes the arrest of 4 individuals in the United Kingdom linked to the running of the site, including the original developer of the service.
The LabHost platform, previously available on the open web, has been shut down.
The Investigation
This international investigation was led by the UK’s London Metropolitan Police, with the support of Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce (J-CAT) hosted at its headquarters.
Europol has supported this case since September 2023. An operational sprint was organized at its headquarters with all the countries involved so that the national investigators could identify and develop intelligence on the users and victims in their own countries. During the action phase, a Europol specialist supported the Dutch National Police with their enforcement actions.
Commoditising Phishing Attacks
Cybercrime-as-a-service has become a rapidly growing business model in the criminal landscape whereby threat actors rent or sell tools, expertise, or services to other cybercriminals to commit their attacks. While this model is well established with ransomware groups, it has also been adopted in other aspects of cybercrime, such as phishing attacks.
LabHost had become a significant tool for cybercriminals around the world. For a monthly subscription, the platform provided phishing kits, infrastructure for hosting pages, interactive functionality for directly engaging with victims, and campaign overview services.
The investigation uncovered at least 40,000 phishing domains linked to LabHost, which had some 10,000 users worldwide.
With a monthly fee averaging $249, LabHost would offer a range of illicit services which were customisable and could be deployed with a few clicks. Depending on the subscription, criminals were provided an escalating scope of targets from financial institutions, postal delivery services and telecommunication services providers, among others. Labhost offered a menu of over 170 fake websites providing convincing phishing pages for its users to choose from.
What made LabHost particularly destructive was its integrated campaign management tool named LabRat. This feature allowed cybercriminals deploying the attacks to monitor and control those attacks in real-time. LabRat was designed to capture two-factor authentication codes and credentials, allowing the criminals to bypass enhanced security measures.
Easily Accessible, Yet Still A Crime
Platforms such as LabHost make cybercrime more easily accessible for unskilled hackers, significantly expanding the pool of threat actors.
Yet, however user-friendly the service portrays itself to be, its malicious use constitutes an illegal activity – and the penalties can be severe.
A vast amount of data gathered throughout the investigation is now in the possession of law enforcement. This data will be used to support ongoing international operational activities focused on targeting the malicious users of this phishing platform.
Participating Agencies and Countries
The following authorities have taken part in the investigation:
- Australia: Australian Federal Police-led Joint Policing Cybercrime Coordination Centre;
- Austria: Criminal Intelligence Service (Bundeskriminalamt);
- Belgium: Federal Judicial Police Brussels (Police judiciaire fédérale Bruxelles/ Federale gerechtelijke politie Brussel);
- Finland: National Police (Poliisi);
- Ireland: An Garda Siochana;
- Netherlands: Central Netherlands Police (Politie Midden-Nederland);
- New Zealand: New Zealand Police;
- Lithuania: Lithuania Police;
- Malta: Malta Police Force (Il-Korp tal-Pulizija ta’ Malta);
- Poland: Central Office for Combating Cybercrime (Centralne Biuro Zwalczania Cyberprzestępczości);
- Portugal: Judicial Police (Polícia Judiciária);
- Romania: Romanian Police (Poliția Română);
- Spain: National Police (Policía Nacional);
- Sweden: Swedish Police Authority (Polisen);
- United Kingdom: London Metropolitan Police;
- United States: United States Secret Service (USSS) and Federal Bureau of Investigation (FBI);
- Czechia: Bureau of Criminal Police and Investigation Service;
- Estonia: Estonian Police and Border Guard Board;
- Canada: Royal Canadian Mounted Police.
![Stargrew_0.png[1] Global Law Enforcement Collaboration Takes Down 'LabHost' Phishing-As-A-Service Platform - 2024](https://scamsnow.com/wp-content/uploads/2024/05/Stargrew_0.png1_-1024x576.webp)
According to the UK’s Metropolitan Police
A website used by more than 2,000 criminals to defraud victims worldwide has been infiltrated in the Met’s latest joint operation to tackle large-scale online fraud.
‘LabHost’ is a service which was set up in 2021 by a criminal cyber network. It enabled the creation of “phishing” websites designed to trick victims into revealing personal information such as email addresses, passwords, and bank details.
Users were able to log on and choose from existing sites or request bespoke pages replicating those of trusted brands including banks, healthcare agencies and postal services.
But LabHost has now been infiltrated and disrupted as the result of a worldwide operation led by the Met.
Work began in June 2022 after detectives received crucial intelligence about LabHost’s activity from the Cyber Defence Alliance. Once the scale of site and the linked fraud became clear the Met’s Cyber Crime Unit joined forces with the National Crime Agency, City of London Police, Europol, Regional Organised Crime Units (ROCUs) across the country and other international police forces to take action.
Partners including Chainalysis, Intel 471, Microsoft, The Shadowserver Foundation and Trend Micro have also been at the centre of our efforts to bring down this platform.
Between Sunday, 14 April and Wednesday, 17 April a total of 37 suspects were arrested across the UK and by international law enforcement agencies. This included arrests at both Manchester and Luton airports, as well as in Essex and London. Both in the UK and across the world over 70 addresses were searched.
On Wednesday, 17 April LabHost and its linked fraudulent sites were disrupted and existing information was replaced with a message stating law enforcement has seized the services.
History of the operation
After being set up in 2021, LabHost quickly gained a criminal user base. By the beginning of 2024 more than 40,000 fraudulent sites had been created and 2,000 users were registered and paying a monthly subscription fee. Those subscribing to the ‘worldwide membership’, meaning they could target victims internationally, paid between £200 and £300 a month.
Since creation LabHost has received just under £1 million ($1,173,000) in payments from criminal users, many of whom Met cyber-crime detectives have now been able to identify. Some have been arrested in this week’s activity, others are now the focus of the ongoing investigation and have been warned we’re now working to track them down.
Shortly after the platform was disrupted, 800 users received a message telling them we know who they are and what they’ve been doing. We’ve shown them we know how much they’ve paid to LabHost, how many different sites they’ve accessed and how many lines of data they’ve received. Many of these individuals will remain the focus of investigation over the coming weeks and months.
Detectives have so far established that just under 70,000 individual UK victims have entered their details into one of LabHost’s fraudulent sites. Globally, the service has obtained 480,000 card numbers, 64,000 PIN numbers, as well as more than one million passwords used for websites and other online services. The total number of victims is likely to be even higher than already established and work is ongoing to identify and support as many as possible.
As of Thursday, 18 April detectives have contacted up to 25,000 victims in the UK to tell them their data has been compromised. Each and every one of those cases has been reported to both Action Fraud and UK Finance and every victim has been given advice about next steps and how to further protect their data. A team of officers from the Met will be stood up to provide personalised support to any victims who want further help and advice.
Latest step in targeting large-scale online fraud
This operation is the latest in a series of activity by law enforcement to tackle significant, international online fraud.
Policing and partners continue to meet the growing threat through increasingly joined up and sophisticated operations reaching across the globe.
In November 2022 the Met arrested more than 130 suspects as part of Operation Elaborate. An estimated 200,000 victims were targeted by a scam stealing millions from the public via fake bank phone calls.
In February 2024, the National Crime Agency led Operation Cronos which disrupted LockBit, the world’s most harmful cyber-crime group. LockBit ransomware attacks targeted thousands of victims around the world and caused billions of pounds worth of damage. The NCA infiltrated and took control of LockBit’s systems and dark website, compromising their entire operation. The Agency obtained thousands of decryption keys to help victims recover encrypted data.
Each operation focused on tackling a different type of online fraud, but at the heart was a platform being used by criminals who believed it was impenetrable by law enforcement.
Dame Lynne Owens, Deputy Commissioner of the Metropolitan Police Service, said: “You are more likely to be a victim of fraud than any other crime. In addition to the financial impact, it undermines the public’s confidence in the tools and technology they need to use in daily life. Our collective approach should ensure suspects feel that same level of distrust in their own criminal environment.
“Online fraudsters think they can act with impunity. They believe they can hide behind digital identities and platforms such as LabHost and have absolute confidence these sites are impenetrable by policing.
“But this operation and others over the last year show how law enforcement worldwide can, and will, come together with one another and private sector partners to dismantle international fraud networks at source. Our approach is to be more precise and targeted with a clear focus on those enabling online fraud to be carried out on an international scale.”
Adrian Searle, Director of the National Economic Crime Centre (NECC) in the NCA, said: “Fraud is a terrible crime that impacts victims both financially and psychologically, undermining our collective trust in others and the online services on which we all rely.
“Together with cyber crime, it makes up around 50% of all crime in England and Wales. Recognising the scale and nature of the threat, law enforcement are working evermore closely together, both here and overseas, to target the fraudsters and the technology they are exploiting.
“This operation again demonstrates that UK law enforcement has the capability and intent to identify, disrupt and completely compromise criminal services that are targeting the UK on an industrial scale.
“Alongside law enforcement action, we also encourage everyone to protect themselves and their online accounts, by creating strong, unique passwords, using two step verification if offered and activating their browser’s password manager. You can also visit the Stop Think Fraud website for lots of really useful advice.
“If you have doubts about a message or call, contact the organisation directly to check. Use contact details from their official website”.
Temporary Commander Oliver Shaw from City of London Police, said: “Collaborative operations like this are vitally important in the global fight against fraud and cyber crime.
“As the national lead force for fraud, we were able to support the operation by providing intelligence derived from reports made to Action Fraud. We continue to support the Metropolitan Police Service, Regional Organised Crime Units (ROCUs) and forces across the UK, to put cyber criminal fraudsters on the back foot.
“If you think you have been a victim of fraud, contact your bank immediately and report to Action Fraud at actionfraud.police.uk or call 0300 123 2040.”
Amy Hogan-Burney, General Manager, Cybersecurity Policy & Protection at Microsoft said: “Today’s action led by the United Kingdom’s Metropolitan Police Service shows the impact we can have in the fight against cybercrime when we work together. We must continue to work together and leverage the immense skills of industry and governments to defeat these threats.”
A spokesperson for the Cyber Defence Alliance said: “The partnership with the Cyber Defence Alliance and law enforcement continues to develop. We have together, once again, been able to disrupt a major international criminal platform and prevented more people falling victim to these scams.
“In the digital world we live in, our alliance will continue to work with law enforcement to combat the growing threat of online fraud which impacts millions of people across the globe.”
Security Minister Tom Tugendhat said: “Fraud is an international crime demanding a global approach.
“This operation is a fantastic demonstration of law enforcement agencies around the world coming together to crack down on criminals trying to take advantage of people in the UK.
“I am grateful to the Metropolitan Police, the National Crime Agency and our National Fraud Squad for their action to infiltrate this criminal platform offering off-the-shelf phishing services.
“Fraud is already down 13% thanks to the action we’ve taken. We will continue our efforts to keep taking the fight to fraudsters.”
Information for victims contacted by the Met before Thursday, 18 April.
If you would like to speak to our officers for any further information please call 02072308603. This telephone line will be open from 8am to 8pm daily until Sunday 21 April 2024. Alternatively, please email CyberProtect at the Met or visit The Met Police Website Cyber Protect.
A man has been charged with offences relating to this matter.
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
More Law Enforcement Actions Related Information:
- EUROPOL Action Against European Money Laundering Operations – 2024 (scamsnow.com)
- Qakbot Botnet Infrastructure Shattered After An International Operation Led By FBI/Europol Takes It Down (scamsnow.com)
- Europol Arrests 70 Phone Scammers Plus Kingpin (scamsnow.com)
- EUROPOL Money Mule Action 2023 – Over 10,000 Identified (scamsnow.com)
- Euro Phishing Gang Shut Down Europol & Partners – 2023 (scamsnow.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
SCARS LINKS: AgainstScams.org RomanceScamsNOW.com ContraEstafas.org ScammerPhotos.com Anyscam.com ScamsNOW.com
reporting.AgainstScams.org support.AgainstScams.org membership.AgainstScams.org donate.AgainstScams.org shop.AgainstScams.org
youtube.AgainstScams.org linkedin.AgainstScams.org facebook.AgainstScams.org
TABLE OF CONTENTS
- The Takedown of the LabHost Platform is a Major Step in Reducing Phishing Scams
- About This Article
- Law Enforcement from 19 Countries Severely Disrupted one of the world’s largest Phishing-as-a-service platforms known as ‘LabHost’
- Facilitating Phishing Scams
- The Investigation
- Commoditising Phishing Attacks
- Easily Accessible, Yet Still A Crime
- Participating Agencies and Countries
- According to the UK’s Metropolitan Police
- LabHost Arrests
- More Law Enforcement Actions Related Information:
CATEGORIES
![NavyLogo@4x-81[1] Global Law Enforcement Collaboration Takes Down 'LabHost' Phishing-As-A-Service Platform - 2024](https://scamsnow.com/wp-content/uploads/2025/04/NavyLogo@4x-811.png)
ARTICLE META
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims.
- SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
- SCARS Institute now offers a free recovery learning program at www.SCARSeducation.org.
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery.
If you are looking for local trauma counselors, please visit counseling.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
Statement About Victim Blaming
Some of our articles discuss various aspects of victims. This is both about better understanding victims (the science of victimology) and their behaviors and psychology. This helps us to educate victims/survivors about why these crimes happened and not to blame themselves, better develop recovery programs, and help victims avoid scams in the future. At times, this may sound like blaming the victim, but it does not blame scam victims; we are simply explaining the hows and whys of the experience victims have.
These articles, about the Psychology of Scams or Victim Psychology – meaning that all humans have psychological or cognitive characteristics in common that can either be exploited or work against us – help us all to understand the unique challenges victims face before, during, and after scams, fraud, or cybercrimes. These sometimes talk about some of the vulnerabilities the scammers exploit. Victims rarely have control of them or are even aware of them, until something like a scam happens, and then they can learn how their mind works and how to overcome these mechanisms.
Articles like these help victims and others understand these processes and how to help prevent them from being exploited again or to help them recover more easily by understanding their post-scam behaviors. Learn more about the Psychology of Scams at www.ScamPsychology.org
SCARS INSTITUTE RESOURCES:
If You Have Been Victimized By A Scam Or Cybercrime
♦ If you are a victim of scams, go to www.ScamVictimsSupport.org for real knowledge and help
♦ SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org/register – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
♦ Enroll in SCARS Scam Survivor’s School now at www.SCARSeducation.org
♦ To report criminals, visit https://reporting.AgainstScams.org – we will NEVER give your data to money recovery companies like some do!
♦ Follow us and find our podcasts, webinars, and helpful videos on YouTube: https://www.youtube.com/@RomancescamsNowcom
♦ Learn about the Psychology of Scams at www.ScamPsychology.org
♦ Dig deeper into the reality of scams, fraud, and cybercrime at www.ScamsNOW.com and www.RomanceScamsNOW.com
♦ Scam Survivor’s Stories: www.ScamSurvivorStories.org
♦ For Scam Victim Advocates visit www.ScamVictimsAdvocates.org
♦ See more scammer photos on www.ScammerPhotos.com
You can also find the SCARS Institute’s knowledge and information on Facebook, Instagram, X, LinkedIn, and TruthSocial
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this and other SCARS articles are intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
Note about Mindfulness: Mindfulness practices have the potential to create psychological distress for some individuals. Please consult a mental health professional or experienced meditation instructor for guidance should you encounter difficulties.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here
If you are in crisis, feeling desperate, or in despair, please call 988 or your local crisis hotline – international numbers here.
More ScamsNOW.com Articles
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish. Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors’ experience. You can do Google searches, but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.



![Global Law Enforcement Collaboration Takes Down 'LabHost' Phishing-As-A-Service Platform - 2024 2 Being A Victim - Labeling Theory & What It Means For Victims Of Scams Or Anyone! - 2023 [UPDATED] - on SCARS ScamsNOW.com](https://scamsnow.com/wp-content/uploads/2024/05/Being-a-Victim.png)



























![scars-institute[1] Global Law Enforcement Collaboration Takes Down 'LabHost' Phishing-As-A-Service Platform - 2024](https://scamsnow.com/wp-content/uploads/2025/04/scars-institute1.png)

![niprc1.png1_-150×1501-1[1] Global Law Enforcement Collaboration Takes Down 'LabHost' Phishing-As-A-Service Platform - 2024](https://scamsnow.com/wp-content/uploads/2025/04/niprc1.png1_-150x1501-11.webp)