LockBit Ransomware Shut Down By Combined Global Law Enforcement
Global Operation Chronos Shuts Down LockBit Ransomware
Cybercrime News
Authors:
• SCARS Editorial Team – Society of Citizens Against Relationship Scams Inc.
• Europol
• U.S. Department of Justice
About This Article
FBI and Europol reports LockBit as the most deployed ransomware globally, with operations disrupted by law enforcement across ten countries. LockBit, infamous for causing extensive financial damage, saw its criminal activities severely compromised.
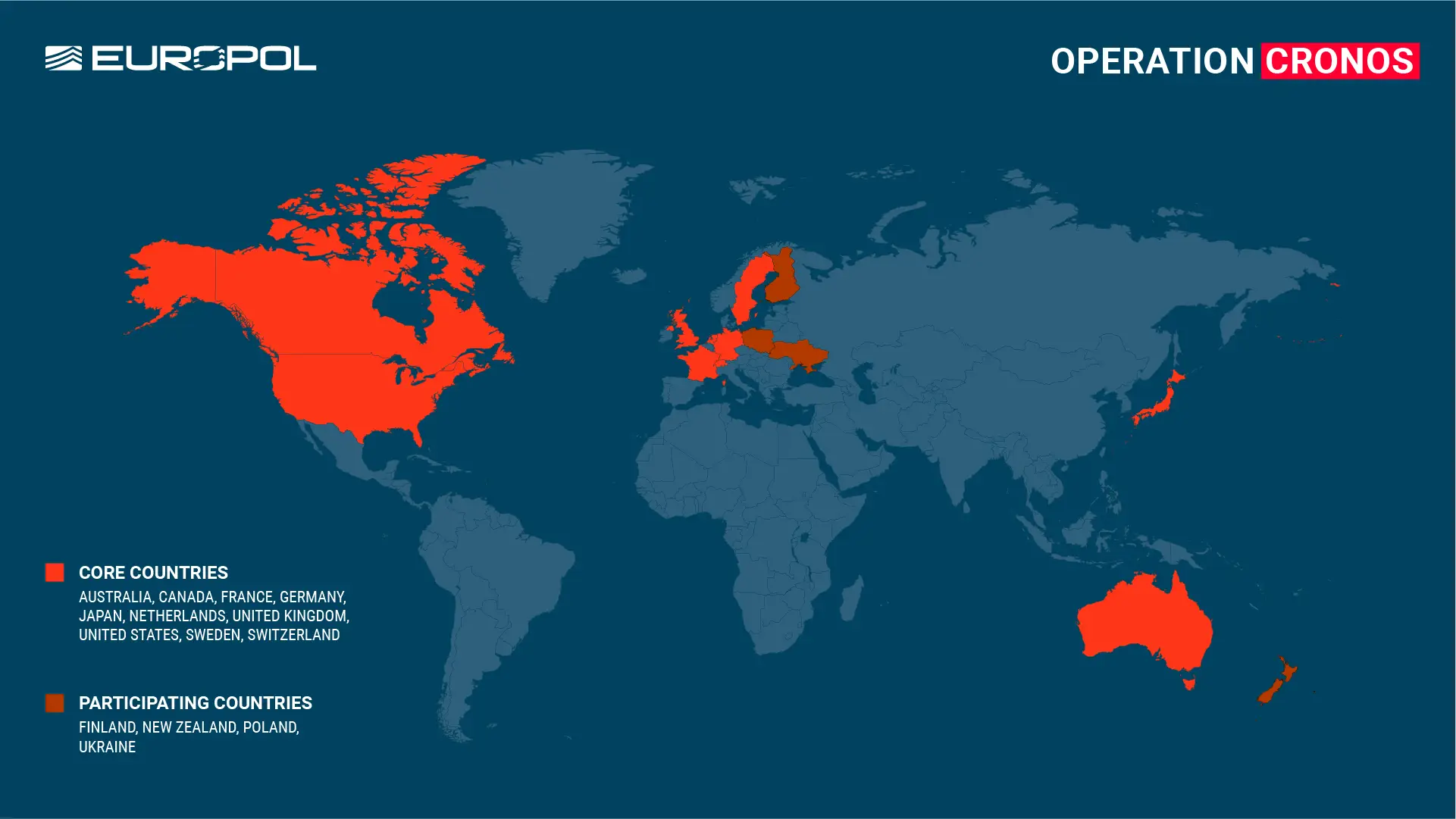
The international effort, led by the UK’s National Crime Agency under ‘Operation Cronos’, coordinated by Europol, dismantled LockBit’s infrastructure, including 34 seized servers. Arrests were made in Poland and Ukraine, with warrants issued by French and US authorities. Over 200 cryptocurrency accounts linked to the group were frozen.
This coordinated action reflects a commitment to combat ransomware and disrupt criminal networks, showcasing the effectiveness of international cooperation in combating cybercrime.

Global Law Enforcement Disrupts the World’s Biggest Ransomware Operation: LockBit
Operation Cronos: Dismantling the LockBit Ransomware Empire
Cybersecurity experts around the world took a sigh of relief last week with the news of Operation Cronos, a joint international operation led by the FBI and Europol that successfully disrupted the infamous LockBit ransomware gang.
LockBit, known for its aggressive tactics and targeting of high-profile victims, had become a major cybersecurity threat. The group employed a “RaaS” (Ransomware-as-a-Service) model, meaning they provided ransomware tools and infrastructure to affiliates who carried out attacks in exchange for a share of the ransom. This decentralized structure made them difficult to track and dismantle.
Unveiling the LockBit Network
Operation Cronos, a culmination of months of collaborative investigation, targeted the core infrastructure of LockBit. Utilizing a combination of technical expertise and international cooperation, authorities were able to:
- Seize control of LockBit’s main administration platform: This effectively crippled the group’s communication and control over its affiliates, disrupting their attack operations.
- Identify and arrest key LockBit figures: Apprehensions of key actors further disrupted the organization and sent a strong message to other cybercriminals.
- Gather valuable intelligence: Seized data provided insights into LockBit’s operations, aiding in future investigations and prevention efforts.
Impact and Implications
This operation represents a significant victory in the fight against cybercrime. The disruption of LockBit will:
- Reduce the number of ransomware attacks: With central infrastructure compromised, future attacks become less likely.
- Discourage potential affiliates: The arrests and dismantling of the core group serve as a deterrent to others considering involvement in ransomware activities.
- Boost international cooperation: Operation Cronos highlights the effectiveness of collaborative efforts between law enforcement agencies across borders.
Taskforce Operation Cronos
This activity forms part of an ongoing, concerted campaign by the international Operation Cronos task force to target and disrupt LockBit ransomware. The following authorities are part of this task force:
- France: National Gendarmerie (Gendarmerie Nationale – Unité nationale cyber C3N)
- Germany: State Bureau of Criminal Investigation Schleswig-Holstein(LKA Schleswig-Holstein), Federal Criminal Police Office (Bundeskriminalamt)
- The Netherlands: National Police (Team Cybercrime Zeeland-West-Brabant, Team Cybercrime Oost-Brabant, Team High Tech Crime) & Public Prosecutor’s Office Zeeland-West-Brabant
- Sweden: Swedish Police Authority
- Australia: Australian Federal Police (AFP)
- Canada: Royal Canadian Mounted Police (RCMP)
- Japan: National Police Agency (警察庁)
- United Kingdom: National Crime Agency (NCA), South West Regional Organised Crime Unit (South West ROCU)
- United States: U.S. Department of Justice (DOJ), Federal Bureau of Investigation (FBI) Newark
- Switzerland: Swiss Federal Office of Police (fedpol), Public Prosecutor’s Office of the canton of Zurich, Zurich Cantonal Police
The successful action was made possible thanks to the support of the following countries:
- Finland: National Police (Poliisi)
- Poland: Central Cybercrime Bureau Cracow (Centralne Biuro Zwalczania Cyberprzestępczości – Zarząd w Krakowie)
- New Zealand: New Zealand Police (Nga Pirihimana O Aotearoa)
- Ukraine: Prosecutor General`s office of Ukraine (Офіс Генерального прокурора України), Cybersecurity Department of the Security Service of Ukraine (Служба безпеки України), National Police of Ukraine (Національна поліція України)
Report it to the Police
This investigation shows that law enforcement has the capabilities to disrupt high-harm cybercriminals and reduce the ransomware threat. However, continued victim and private sector engagement is key to us continuing this work.
The first step to putting cybercriminals behind bars is to report cybercrime when it happens. The earlier people report the quicker law enforcement is able to assess new methodologies and limit the damage they can cause.
victims of LockBit should contact the FBI at https://lockbitvictims.ic3.gov for further information. Additional details on protecting networks against LockBit ransomware are available at StopRansomware.gov.
According to Europol
LockBit was the most deployed ransomware variant across the world
In a significant breakthrough in the fight against cybercrime, law enforcement from 10 countries has disrupted the criminal operation of the LockBit ransomware group at every level, severely damaging their capability and credibility.
LockBit is widely recognized as the world’s most prolific and harmful ransomware, causing billions of euros worth of damage.
This international sweep follows a complex investigation led by the UK’s National Crime Agency in the framework of an international task force known as ‘Operation Cronos’, coordinated at the European level by Europol and Eurojust.
The months-long operation has resulted in the compromise of LockBit’s primary platform and other critical infrastructure that enabled their criminal enterprise. This includes the takedown of 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States and the United Kingdom.
In addition, two LockBit actors have been arrested in Poland and Ukraine at the request of the French judicial authorities. Three international arrest warrants and five indictments have also been issued by the French and U.S. judicial authorities.
Authorities have frozen more than 200 cryptocurrency accounts linked to the criminal organization, underscoring the commitment to disrupt the economic incentives driving ransomware attacks.
The UK’s National Crime Agency has now taken control of the technical infrastructure that allows all elements of the LockBit service to operate, as well as their leak site on the dark web, on which they previously hosted the data stolen from victims in ransomware attacks.
At present, a vast amount of data gathered throughout the investigation is now in the possession of law enforcement. This data will be used to support ongoing international operational activities focused on targeting the leaders of this group, as well as developers, affiliates, infrastructure, and criminal assets linked to these criminal activities.
The World’s Most Harmful Ransomware
LockBit first emerged at the end of 2019, first calling itself ‘ABCD’ ransomware. Since then, it has grown rapidly and in 2022 it became the most deployed ransomware variant across the world.
The group is a ‘ransomware-as-a-service’ operation, meaning that a core team creates its malware and runs its website, while licensing out its code to affiliates who launch attacks.
LockBit’s attack presence is seen globally, with hundreds of affiliates recruited to conduct ransomware operations using LockBit tools and infrastructure. Ransom payments were divided between the LockBit core team and the affiliates, who received on average three-quarters of the ransom payments collected.
The ransomware group is also infamous for experimenting with new methods for pressuring their victims into paying ransoms. Triple extortion is one such method which includes the traditional methods of encrypting the victim’s data and threatening to leak it, but also incorporates Distributed Denial-of-Service (DDoS) attacks as an additional layer of pressure.
The gang’s move to triple extortion was partly influenced by a DDoS attack they themselves experienced, which impeded their ability to publish stolen data. In response, LockBit enhanced their infrastructure to resist such attacks.
This infrastructure is now under law enforcement control, and more than 14 000 rogue accounts responsible for exfiltration or infrastructure have been identified and referred for removal by law enforcement.
Europol’s coordinating role
With countries involved on either side of the world, Europol – which hosts the world’s biggest network of liaison officers from EU Member States – played a central role in coordinating the international activity.
Europol’s European Cybercrime Centre (EC3) organised 27 operational meetings, and four technical one-week sprints to develop the investigative leads in preparation of the final phase of the investigation.
Europol also provided analytical, crypto-tracing and forensic support to the investigation, and facilitated the information exchange in the framework of the Joint Cybercrime Action Taskforce (J-CAT) hosted at its headquarters. In addition, three Europol experts were deployed to the command post in London during the action phase.
In total, over 1 000 operational messages have been exchanged on this case via Europol’s secure information channel SIENA, making it one of EC3’s most active investigations.
The case was opened at Eurojust in April 2022 at the request of the French authorities. Five coordination meetings were hosted by the Agency to facilitate judicial cooperation and to prepare for the joint action.
Decryption tools available on No More Ransom
With Europol’s support, the Japanese Police, the National Crime Agency and the Federal Bureau of Investigation have concentrated their technical expertise to develop decryption tools designed to recover files encrypted by the LockBit Ransomware.
These solutions have been made available for free on the ‘No More Ransom’ portal, available in 37 languages. So far, more than 6 million victims across the globe have benefitted from No More Ransom which contains over 120 solutions capable of decrypting more than 150 different types of ransomware.
U.S. and U.K. Disrupt LockBit Ransomware Variant
According to the U.S. Department of Justice
U.S. Indictment Charges Two Russian Nationals with Attacks Against Multiple U.S. and International Victims; FBI Seizes Infrastructure; and Department of Treasury Takes Additional Action Against LockBit
The Department of Justice joined the United Kingdom and international law enforcement partners in London today to announce the disruption of the LockBit ransomware group, one of the most active ransomware groups in the world that has targeted over 2,000 victims, received more than $120 million in ransom payments, and made ransom demands totaling hundreds of millions of dollars.
The U.K. National Crime Agency’s (NCA) Cyber Division, working in cooperation with the Justice Department, Federal Bureau of Investigation (FBI), and other international law enforcement partners disrupted LockBit’s operations by seizing numerous public-facing websites used by LockBit to connect to the organization’s infrastructure and seizing control of servers used by LockBit administrators, thereby disrupting the ability of LockBit actors to attack and encrypt networks and extort victims by threatening to publish stolen data.
“For years, LockBit associates have deployed these kinds of attacks again and again across the United States and around the world. Today, U.S. and U.K. law enforcement are taking away the keys to their criminal operation,” said Attorney General Merrick B. Garland. “And we are going a step further — we have also obtained keys from the seized LockBit infrastructure to help victims decrypt their captured systems and regain access to their data. LockBit is not the first ransomware variant the Justice Department and its international partners have dismantled. It will not be the last.”
Additionally, the NCA, in cooperation with the FBI and international law enforcement partners, has developed decryption capabilities that may enable hundreds of victims around the world to restore systems encrypted using the LockBit ransomware variant. Beginning today, victims targeted by this malware are encouraged to contact the FBI at https://lockbitvictims.ic3.gov/ to enable law enforcement to determine whether affected systems can be successfully decrypted.
“Today’s actions are another down payment on our pledge to continue dismantling the ecosystem fueling cybercrime by prioritizing disruptions and placing victims first,” said Deputy Attorney General Lisa Monaco. “Using all our authorities and working alongside partners in the United Kingdom and around the world, we have now destroyed the online backbone of the LockBit group, one of the world’s most prolific ransomware gangs. But our work does not stop here: together with our partners, we are turning the tables on LockBit — providing decryption keys, unlocking victim data, and pursuing LockBit’s criminal affiliates around the globe.”
The Justice Department also unsealed an indictment obtained in the District of New Jersey charging Russian nationals Artur Sungatov and Ivan Kondratyev, also known as Bassterlord, with deploying LockBit against numerous victims throughout the United States, including businesses nationwide in the manufacturing and other industries, as well as victims around the world in the semiconductor and other industries. Today, additional criminal charges against Kondratyev were unsealed in the Northern District of California related to his deployment in 2020 of ransomware against a victim located in California.
Finally, the Department also unsealed two search warrants issued in the District of New Jersey that authorized the FBI to disrupt multiple U.S.-based servers used by LockBit members in connection with the LockBit disruption. As disclosed by those search warrants, those servers were used by LockBit administrators to host the so-called “StealBit” platform, a criminal tool used by LockBit members to organize and transfer victim data.
“Today, the FBI and our partners have successfully disrupted the LockBit criminal ecosystem, which represents one of the most prolific ransomware variants across the globe,” said FBI Director Christopher A. Wray. “Through years of innovative investigative work, the FBI and our partners have significantly degraded the capabilities of those hackers responsible for launching crippling ransomware attacks against critical infrastructure and other public and private organizations around the world. This operation demonstrates both our capability and commitment to defend our nation’s cybersecurity and national security from any malicious actor who seeks to impact our way of life. We will continue to work with our domestic and international allies to identify, disrupt, and deter cyber threats, and to hold the perpetrators accountable.”
According to the indictment obtained in the District of New Jersey, from at least as early as January 2021, Sungatov allegedly deployed LockBit ransomware against victim corporations and took steps to fund additional LockBit attacks against other victims. Sungatov allegedly deployed LockBit ransomware against manufacturing, logistics, insurance, and other companies located in Minnesota, Indiana, Puerto Rico, Wisconsin, Florida, and New Mexico. Additionally, as early as August 2021, Kondratyev similarly began to allegedly deploy LockBit against multiple victims. Kondratyev, operating under the online alias “Bassterlord,” allegedly deployed LockBit against municipal and private targets in Oregon, Puerto Rico, and New York, as well as additional targets located in Singapore, Taiwan, and Lebanon. Both Sungatov and Kondratyev are alleged to have joined in the global LockBit conspiracy, also alleged to have included Russian nationals Mikhail Pavlovich Matveev and Mikhail Vasiliev, as well as other LockBit members, to develop and deploy LockBit ransomware and to extort payments from victim corporations.
“Today’s indictment, unsealed as part of a global coordinated action against the most active ransomware group in the world, brings to five the total number of LockBit members charged by my office and our FBI and Computer Crime and Intellectual Property Section partners for their crimes,” said U.S. Attorney Philip R. Sellinger for the District of New Jersey. “And, even with today’s disruption of LockBit, we will not stop there. Our investigation will continue, and we remain as determined as ever to identify and charge all of LockBit’s membership — from its developers and administrators to its affiliates. We will put a spotlight on them as wanted criminals. They will no longer hide in the shadows.”
With the indictment unsealed today, a total of five LockBit members have now been charged for their participation in the LockBit conspiracy. In May 2023, two indictments were unsealed in Washington, D.C., and the District of New Jersey charging Matveev with using different ransomware variants, including LockBit, to attack numerous victims throughout the United States, including the Washington, D.C., Metropolitan Police Department. Matveev is currently the subject of a reward of up to $10 million through the U.S. Department of State’s Transnational Organized Crime Rewards Program, with information accepted through the FBI tip website at https://tips.fbi.gov. In November 2022, a criminal complaint was filed in the District of New Jersey charging Vasiliev in connection with his participation in the LockBit global ransomware campaign. Vasiliev, a dual Russian-Canadian national, is currently in custody in Canada awaiting extradition to the United States. In June 2023, Russian national Ruslan Magomedovich Astamirov was charged by criminal complaint in the District of New Jersey for his participation in the LockBit conspiracy, including his deployment of LockBit against victims in Florida, Japan, France, and Kenya. Astamirov is currently in custody in the United States awaiting trial.
Kondratyev, according to the indictment obtained in the Northern District of California and unsealed today, is also charged with three criminal counts arising from his use of the Sodinokibi, also known as REvil, ransomware variant to encrypt data, exfiltrate victim information, and extort a ransom payment from a corporate victim based in Alameda County, California.
The LockBit ransomware variant first appeared around January 2020 and, leading into today’s operation, had grown into one of the most active and destructive variants in the world. LockBit members have executed attacks against more than 2,000 victims in the United States and around the world, making at least hundreds of millions of U.S. dollars in ransom demands and receiving over $120 million in ransom payments. The LockBit ransomware variant, like other major ransomware variants, operates in the “ransomware-as-a-service” (RaaS) model, in which administrators, also called developers, design the ransomware, recruit other members — called affiliates — to deploy it, and maintain an online software dashboard called a “control panel” to provide the affiliates with the tools necessary to deploy LockBit. Affiliates, in turn, identify and unlawfully access vulnerable computer systems, sometimes through their own hacking or at other times by purchasing stolen access credentials from others. Using the control panel operated by the developers, affiliates then deploy LockBit within the victim computer system, allowing them to encrypt and steal data for which a ransom is demanded to decrypt or avoid publication on a public website maintained by the LockBit developers, often called a data leak site.
The FBI Newark Field Office is investigating the LockBit ransomware variant.
Assistant U.S. Attorneys Andrew M. Trombly, David E. Malagold, and Vinay Limbachia for the District of New Jersey and Trial Attorneys Jessica C. Peck, Debra Ireland, and Jorge Gonzalez of the Criminal Division’s Computer Crime and Intellectual Property Section are prosecuting the charges against Sungatov and Kondratyev unsealed today in the District of New Jersey. The Justice Department’s Cybercrime Liaison Prosecutor to Eurojust and Office of International Affairs also provided significant assistance.
The disruption announced today was the result of a joint operation between the FBI; NCA South West Regional Organised Crime Unit; France’s Gendarmerie Nationale Cyberspace Command; Germany’s Landeskriminalamt Schleswig-Holstein and the Bundeskriminalamt; Switzerland’s Federal Office of Police, Public Prosecutor’s Office of the Canton of Zurich, and Zurich Cantonal Police; Japan’s National Policy Agency; Australian Federal Police; Sweden’s Polismyndighetens; Royal Canadian Mounted Police; Politie Dienst Regionale Recherche Oost-Brabant of the Netherlands; Finland’s Poliisi; Europol; and Eurojust.
The FBI Phoenix Field Office and Assistant U.S. Attorney Helen L. Gilbert are investigating and prosecuting the case against Kondratyev in the Northern District of California.
Additionally, the Department of the Treasury’s Office of Foreign Assets Control announced today that it is designating Sungatov and Kondratyev for their roles in launching cyberattacks.
Please Rate This Article
Please Leave Us Your Comment
Also, tell us of any topics we might have missed.
Thank you for your comment. You may receive an email to follow up. We never share your data with marketers.
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment above!
More Related to Ransomware:
- Ragnar Locker Ransomware Gang Taken Down 2023 (scamsnow.com)
- Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland (scamsnow.com)
- Ransomware – Ukraine Gets Serious About Combatting Homegrown Cybercrime 2023 (scamsnow.com)
- Qakbot Botnet Infrastructure Shattered After An International Operation Led By FBI/Europol Takes It Down (scamsnow.com)
- Negotiating Ransomware, Data Breach, & Cybercrime Payments 2024 (romancescamsnow.com)
- Calisto Group Organization – Ransomware & Cybercrime Gang – 2023 (romancescamsnow.com)
- BazarCall Scams: Call Centers Playing A Roll In Phishing & Ransomware Attacks (romancescamsnow.com)
- Ransomware Guide – A U.S. Government Report – DHS CISA December 2020 (romancescamsnow.com)
- SCARS™ CYBER BASICS: Ransomware (romancescamsnow.com)
- SCARS™ Cybersecurity Guide: Protecting Against Ransomware (romancescamsnow.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment above!
SCARS LINKS: AgainstScams.org RomanceScamsNOW.com ContraEstafas.org ScammerPhotos.com Anyscam.com ScamsNOW.com
reporting.AgainstScams.org support.AgainstScams.org membership.AgainstScams.org donate.AgainstScams.org shop.AgainstScams.org
youtube.AgainstScams.org linkedin.AgainstScams.org facebook.AgainstScams.org
ARTICLE RATING
TABLE OF CONTENTS
CATEGORIES
MOST POPULAR COMMENTED ARTICLES
POPULAR ARTICLES
U.S. & Canada Suicide Lifeline 988
![NavyLogo@4x-81[1]](https://scamsnow.com/wp-content/uploads/2025/04/NavyLogo@4x-811.png)
ARTICLE META
WHAT PEOPLE ARE TALKING ABOUT LATEST SITE COMMENTS
See Comments for this Article at the Bottom of the Page
on The Uniqueness Of Scam Victims Or Fraud Victims – 2024: “Really informative” Jun 28, 08:58
on Samurai Wisdom and Rituals for Clearing the Mind After Scam Trauma – 2025 – [VIDEOS]: “A great guide on how to move forward in our recovery process with a calm mind, cleansed on an ongoing…” Jun 28, 07:34
on Delayed Gratification and Patience in Scam Victim Recovery – 2025 – [VIDEOS]: “We want to recover quickly and… we make new mistakes. How not to speed up the recovery process, how to…” Jun 28, 06:41
on The Unique Injury Of Betrayal Trauma On Scam Victims – 2024: “Primarily because you did not see it coming” Jun 27, 23:57
on Changes In A Scam Victim’s Life: “I really detest the way my trust in others has been affected by the scamming I went through. I used…” Jun 27, 14:47
on The Unique Injury Of Betrayal Trauma On Scam Victims – 2024: “Betrayal Trauma is the worst feeling ever. Why does it seem so much worse when a scammer does that to…” Jun 27, 14:34
on EMDR Therapy For Scam Victims’ Trauma – A Part Of The Recovery Process For Many – 2024: “Very comprehensive article explaining all aspects of EMDR. I’d only heard of it before and now I have a much…” Jun 26, 19:01
on Forgiving Yourself After Surviving a Romance or Investment Scam – 2025: “Thank you for this valuable article. Self-forgiveness was for me the biggest step that led to my recovery. That also…” Jun 26, 17:28
on Counseling And Your Native Language: “These points make perfect sense. I can’t imagine trying to express complex emotions in a second language. I realize many…” Jun 26, 16:05
on Thought-Terminating Cliches – How What You and Others Say Stops Critical Thinking and Recovery for Scam Victims – 2025: “I didn’t realize that these “innocent phrases” clichés ending thoughts, can have such effect / negative -inhibiting / on our…” Jun 26, 14:48
on Scam Victim Resistance In Support Groups Therapy Or Counseling Can Destroy Opportunities For Recovery – 2024: “Working with either a support group or therapist to me means a self commitment to actively participating in the therapy.…” Jun 24, 21:01
on ‘I Just Want To Forget It’ – Denial & Avoidance Are Natural But Will Not Help Scam Victims On Their Path To Recovery From Scams – 2024: “My financial loss, the shock and betrayal of the crime ending all combined to fray my nerves and spend hours…” Jun 24, 20:10
on You Hate Being Told What To Do? How Your Rebellious Mentality Can Sabotage Your Recovery – 2025: “I am a bit of a rebel, and the moment someone tells me to do something, worse, does it even…” Jun 24, 15:04
on You Hate Being Told What To Do? How Your Rebellious Mentality Can Sabotage Your Recovery – 2025: “You are very welcome” Jun 24, 03:01
on You Hate Being Told What To Do? How Your Rebellious Mentality Can Sabotage Your Recovery – 2025: “This is a great article, which makes perfect sense as to why anyone would resist the help offered to them.…” Jun 23, 20:01
on Scam Victims’ Responsibilities – 2021 [Updated 2025]: “Thank you for this article. As I continue my journey, I focus on the here and now and let the…” Jun 21, 16:26
on Scam Victims Avoid Or Escape The Aftermath Of Scams – How Denial And Distraction Avoid Confronting Reality – 2024: “In the earliest days after my crime I felt powerless, helpless and weak. I had been through so much in…” Jun 21, 14:46
on Problems and Opportunities – Thoughts on Psychological Reframing – 2025: “An article that really helped me look at the problems in my life from a different point of view and…” Jun 21, 14:42
on Scam Victims Avoid Or Escape The Aftermath Of Scams – How Denial And Distraction Avoid Confronting Reality – 2024: “Thank you for another great article! This discussion of avoidance and other tactics some can use to deny the existence…” Jun 17, 12:20
on Helping Scam Victims Understand The Social Isolation Risks After A Relationship Scam – 2024: “This article very informatively shows the risk of social isolation especially after a scam. Although I can acknowledge the list…” Jun 17, 11:31
Important Information for New Scam Victims
Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims
SCARS Institute now offers a free recovery program at www.SCARSeducation.org
Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery
If you are looking for local trauma counselors, please visit counseling.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
Statement About Victim Blaming
Some of our articles discuss various aspects of victims. This is both about better understanding victims (the science of victimology) and their behaviors and psychology. This helps us to educate victims/survivors about why these crimes happened and not to blame themselves, better develop recovery programs, and help victims avoid scams in the future. At times, this may sound like blaming the victim, but it does not blame scam victims; we are simply explaining the hows and whys of the experience victims have.
These articles, about the Psychology of Scams or Victim Psychology – meaning that all humans have psychological or cognitive characteristics in common that can either be exploited or work against us – help us all to understand the unique challenges victims face before, during, and after scams, fraud, or cybercrimes. These sometimes talk about some of the vulnerabilities the scammers exploit. Victims rarely have control of them or are even aware of them, until something like a scam happens, and then they can learn how their mind works and how to overcome these mechanisms.
Articles like these help victims and others understand these processes and how to help prevent them from being exploited again or to help them recover more easily by understanding their post-scam behaviors. Learn more about the Psychology of Scams at www.ScamPsychology.org
SCARS INSTITUTE RESOURCES:
If You Have Been Victimized By A Scam Or Cybercrime
♦ If you are a victim of scams, go to www.ScamVictimsSupport.org for real knowledge and help
♦ Enroll in SCARS Scam Survivor’s School now at www.SCARSeducation.org
♦ To report criminals, visit https://reporting.AgainstScams.org – we will NEVER give your data to money recovery companies like some do!
♦ Follow us and find our podcasts, webinars, and helpful videos on YouTube: https://www.youtube.com/@RomancescamsNowcom
♦ Learn about the Psychology of Scams at www.ScamPsychology.org
♦ Dig deeper into the reality of scams, fraud, and cybercrime at www.ScamsNOW.com and www.RomanceScamsNOW.com
♦ Scam Survivor’s Stories: www.ScamSurvivorStories.org
♦ For Scam Victim Advocates visit www.ScamVictimsAdvocates.org
♦ See more scammer photos on www.ScammerPhotos.com
You can also find the SCARS Institute on Facebook, Instagram, X, LinkedIn, and TruthSocial
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this and other SCARS articles are intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
Note about Mindfulness: Mindfulness practices have the potential to create psychological distress for some individuals. Please consult a mental health professional or experienced meditation instructor for guidance should you encounter difficulties.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here
If you are in crisis, feeling desperate, or in despair, please call 988 or your local crisis hotline.
More ScamsNOW.com Articles
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish. Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors’ experience. You can do Google searches, but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.












![scars-institute[1]](https://scamsnow.com/wp-content/uploads/2025/04/scars-institute1.png)
![niprc1.png1_-150×1501-1[1]](https://scamsnow.com/wp-content/uploads/2025/04/niprc1.png1_-150x1501-11.webp)

Leave a Reply