Privacy and security of genetic information: Putting DNA companies to the test
By Lesley Fair, Federal Trade Commission – reprint
Some secrets are so secret that no one knows about them. Until recently that described the secrets locked within our DNA. But a key to consumer confidence in the burgeoning genetic testing marketplace is the extent to which people can depend on a company’s promise that “Your secret’s safe with us.”
In its first case focused on the privacy and security of genetic information, the FTC alleges that San Francisco-based Vitagene, Inc. – now known as 1Health.io – failed to live up to its promises and unfairly changed material privacy terms without customers’ consent. The proposed settlement and other recent actions send a loud-and-clear message that the FTC is fully committed to the protection of consumers’ health information.
After consumers paid between $29 and $259, sent a saliva sample to Vitagene, and answered an online questionnaire about their health history, family history, and lifestyle, the company provided them with a personalized Health Report. The Report included the customer’s full name and an assessment of their risks for developing a host of health problems.
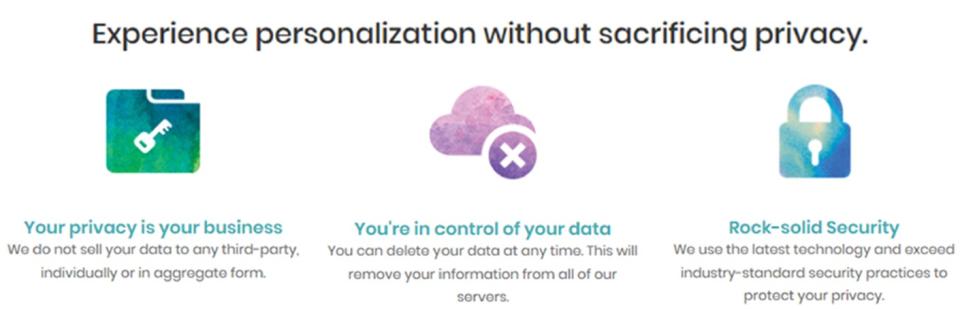
Using images of locks, keys, and secure clouds, the company’s website was replete with claims about the care with which it promised to handle consumers’ genetic information. Here are just a few of the company’s pledges.
- “We use industry-standard security practices to store your DNA sample, your test results, and any other personal data you provide.”
- “Rock–solid Security. We use the latest technology and exceed industry-standard security practices to protect your privacy.”
- “Vitagene collects, processes, and stores your personal information in a responsible, transparent and secure environment that fosters our customers’ trust and confidence.”
- “You’re in control of your data. You can delete your data at any time. This will remove your information from all of our servers.”
- “Three of the ways we protect your privacy: 1. Your results and DNA sample are stored without your name or any other common identifying information. 2. Vitagene destroys your physical DNA saliva sample after it has been analyzed. 3. We don’t share your information with any third party without your explicit consent.”
Nice privacy and security talk, but according to the FTC, Vitagene was more talk than action. You’ll want to read the complaint for details, but part of the story started in the cloud. As a component of its IT infrastructure, Vitagene used a well-known cloud service provider for storing confidential information, including consumers’ Health Reports and DNA data. Vitagene allegedly didn’t use built-in measures to secure the information and instead stored it in “buckets” that made it possible for anyone with internet access to see the detailed Reports of nearly 2,400 Vitagene customers. Also accessible: raw genetic data of at least 227 other customers, sometimes identified by first name. While Vitagene promised to “exceed industry-standard security practices,” the FTC says the company didn’t encrypt that data, didn’t restrict access to it, didn’t monitor access, and didn’t inventory it to help ensure its security. The complaint also charges that Vitagene didn’t take steps to ensure that a lab that analyzed many of the DNA samples had a policy in place to destroy them.
What’s more, the complaint alleges that over a two-year period, Vitagene received three separate warnings that it was storing customers’ health and genetic information in a way that made it publicly accessible. Warning #1: a July 2017 message from the cloud service provider that Vitagene had configured its data “to allow read access from anyone on the Internet.” The email included links to an account console and information about how to restrict access. The response from Vitagene: Crickets.
Warning #2 came from a security company that conducted a web app penetration test in November 2018 and “found that uploaded DNA data was being stored . . . without any access controls.” The complaint alleges that Vitagene again failed to rectify the situation.
Warning #3 was a June 2019 email from a security researcher sent to Vitagene’s support inbox. After the researcher contacted the media, the FTC says the company finally investigated its public exposure of customers’ health information. However, because Vitagene hadn’t monitored who had accessed or downloaded the data, it couldn’t determine who else might have seen the information.
Vitagene’s alleged missteps didn’t end there. In 2020, the company changed its privacy policy by retroactively expanding the types of third parties with which it may share consumers’ data to include grocery chains, dietary supplement manufacturers, and the like. And it did that without notifying customers who provided their data under the former, more restrictive privacy policy and getting their consent.
The complaint charges that the company’s promises that it exceeded industry security standards, stored DNA results without identifying information, deleted data at consumers’ request, and saw to it that physical DNA samples were destroyed were false or misleading. What’s more, the FTC alleges that the company’s after-the-fact privacy policy changes about sharing sensitive personal information with third parties was an unfair practice, in violation of the FTC Act. While Vitagene’s original privacy policy stated that a customer’s access or use of the company’s services after the company posted a revised privacy policy meant that the consumer had accepted the revised terms, that language didn’t excuse Vitagene from its obligation to give notice and get consumers’ consent before making material retroactive changes to its privacy practices. Furthermore, the complaint alleges that Vitagene’s conduct was unfair even though the company has not yet implemented the broader information-sharing practices set forth in its revised privacy policies.
To settle the case, 1health.io has agreed to implement a comprehensive information security program, including every-other-year third-party assessments. In addition, a senior executive must certify annually that the company is complying with the terms of the settlement. The proposed settlement also includes a $75,000 financial remedy. Once the settlement appears in the Federal Register, you’ll have 30 days to file a public comment.
What can other companies take from the FTC’s action?
Sensitive health information – including genetic data – requires intensive care. If your company collects or maintains consumer health information, you’ve raised the bar on the privacy and security standards you must implement. Take particular care to substantiate the promises you make about your data practices. (By the way, if you haven’t read the FTC’s May 2023 Policy Statement on Biometric Information, set aside time now.)
Just because data is in your possession doesn’t mean it’s yours. Collecting consumers’ data doesn’t mean you’re free to do with it as you please. Consumers have a right to know in advance how you intend to use their information and you have the legal obligation to live up to your representations. That means if you want to change your practices down the road, a bait-and-switch modification to your privacy policy won’t suffice. You’ll need consumers’ affirmative express consent for any new uses of their data.
When it comes to security, keeping your data in the cloud doesn’t mean you can keep your head in the clouds. The FTC has long said that storing data in the cloud doesn’t give a company a free pass on security. It’s still your responsibility to take reasonable steps to secure your data – for example, by properly configuring cloud security settings and by inventorying and auditing your cloud storage. As the FTC’s Request for Information about cloud computing makes clear, sellers of cloud technology and the companies that use their services share the responsibility to secure consumers’ personal information.
Respond to credible warnings about potential security lapses. The complaint against Vitagene alleges multiple instances in which the company failed to heed alarms others – including the provider of its cloud storage – had sounded about the security of its cloud-based information. Do you have systems in place to make sure those alerts get to the right people and get the immediate attention they deserve?
More ScamsNOW.com Articles
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims.
- SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
- SCARS Institute now offers a free recovery learning program at www.SCARSeducation.org.
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery.
If you are looking for local trauma counselors, please visit counseling.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
Statement About Victim Blaming
Some of our articles discuss various aspects of victims. This is both about better understanding victims (the science of victimology) and their behaviors and psychology. This helps us to educate victims/survivors about why these crimes happened and not to blame themselves, better develop recovery programs, and help victims avoid scams in the future. At times, this may sound like blaming the victim, but it does not blame scam victims; we are simply explaining the hows and whys of the experience victims have.
These articles, about the Psychology of Scams or Victim Psychology – meaning that all humans have psychological or cognitive characteristics in common that can either be exploited or work against us – help us all to understand the unique challenges victims face before, during, and after scams, fraud, or cybercrimes. These sometimes talk about some of the vulnerabilities the scammers exploit. Victims rarely have control of them or are even aware of them, until something like a scam happens, and then they can learn how their mind works and how to overcome these mechanisms.
Articles like these help victims and others understand these processes and how to help prevent them from being exploited again or to help them recover more easily by understanding their post-scam behaviors. Learn more about the Psychology of Scams at www.ScamPsychology.org
SCARS INSTITUTE RESOURCES:
If You Have Been Victimized By A Scam Or Cybercrime
♦ If you are a victim of scams, go to www.ScamVictimsSupport.org for real knowledge and help
♦ SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org/register – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
♦ Enroll in SCARS Scam Survivor’s School now at www.SCARSeducation.org
♦ To report criminals, visit https://reporting.AgainstScams.org – we will NEVER give your data to money recovery companies like some do!
♦ Follow us and find our podcasts, webinars, and helpful videos on YouTube: https://www.youtube.com/@RomancescamsNowcom
♦ Learn about the Psychology of Scams at www.ScamPsychology.org
♦ Dig deeper into the reality of scams, fraud, and cybercrime at www.ScamsNOW.com and www.RomanceScamsNOW.com
♦ Scam Survivor’s Stories: www.ScamSurvivorStories.org
♦ For Scam Victim Advocates visit www.ScamVictimsAdvocates.org
♦ See more scammer photos on www.ScammerPhotos.com
You can also find the SCARS Institute’s knowledge and information on Facebook, Instagram, X, LinkedIn, and TruthSocial
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this and other SCARS articles are intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
Note about Mindfulness: Mindfulness practices have the potential to create psychological distress for some individuals. Please consult a mental health professional or experienced meditation instructor for guidance should you encounter difficulties.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here
If you are in crisis, feeling desperate, or in despair, please call 988 or your local crisis hotline – international numbers here.
More ScamsNOW.com Articles
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish. Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors’ experience. You can do Google searches, but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.
























![NavyLogo@4x-81[1] Putting DNA Companies to the Test - Privacy and Security of Genetic Information](https://scamsnow.com/wp-content/uploads/2025/04/NavyLogo@4x-811.png)
![scars-institute[1] Putting DNA Companies to the Test - Privacy and Security of Genetic Information](https://scamsnow.com/wp-content/uploads/2025/04/scars-institute1.png)

![niprc1.png1_-150×1501-1[1] Putting DNA Companies to the Test - Privacy and Security of Genetic Information](https://scamsnow.com/wp-content/uploads/2025/04/niprc1.png1_-150x1501-11.webp)