Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland
By SCARS Editorial Team – Society of Citizens Against Relationship Scams Inc., portions Department of Justice and Europol
Cybercriminals Running ‘Bulletproof’ Webhosting Domain Charged in Connection with Facilitation of ‘NetWalker’ Ransomware
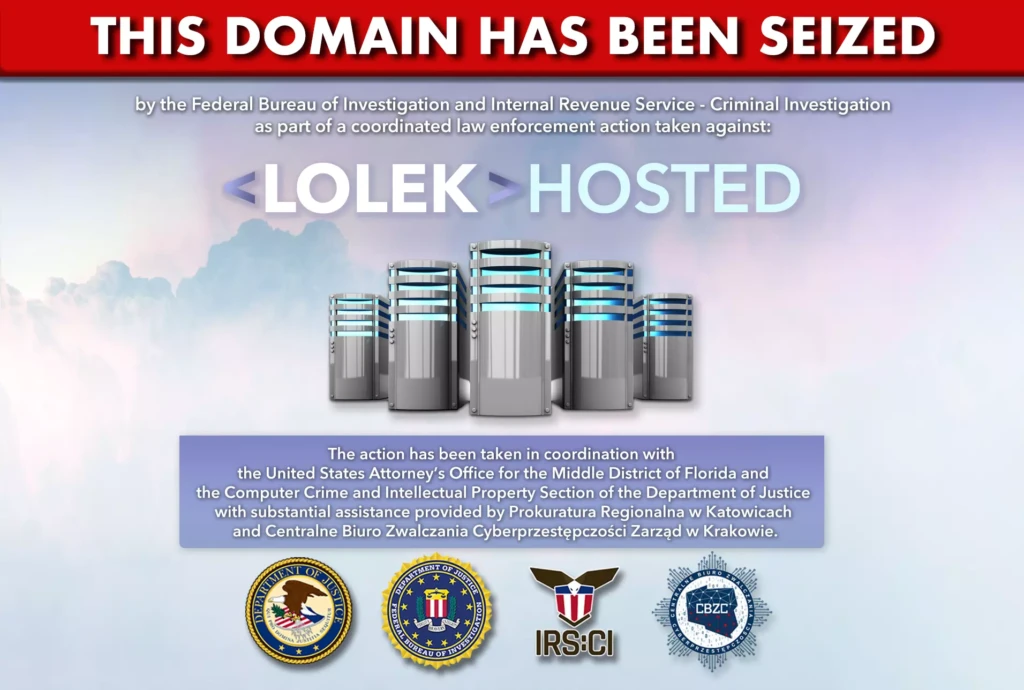
U.S. Authorities, along with Europol Announce Court-Authorized Seizure of LolekHosted.net
5 European cybercriminals were also arrested!
An indictment was unsealed yesterday in Tampa, Florida, USA charging a Polish national with computer fraud conspiracy, wire fraud conspiracy, and international money laundering in connection with the provision of “bulletproof” web hosting services that facilitated the operation of ransomware attacks and the subsequent laundering of the illicit proceeds.
- U.S. Prosecutors seized a ransomware hosting service with the help of European law enforcement, arrested 5, and the U.S. charged its founder with wire fraud and computer fraud over his role in extorting 5,000 bitcoin, worth nearly $146 million at today’s prices, in ransom.
- The service, LolekHosted, allegedly powered ransomware attacks around the world for nearly a decade.
- The Polish founder, Artur Grabowski, remains a fugitive in possession of nearly $22 million in ill-gotten gains, U.S. federal prosecutors allege.
The Story
United States Federal prosecutors announced that they had indicted the alleged mastermind behind a ransomware hosting service, a cybercriminal accused of aiding criminals in accumulating over 5,000 bitcoin in ransom from numerous victims. The current valuation of this Bitcoin stash exceeds $146 million.
He was able to operate for approximately a decade. Artur Grabowski’s LolekHosted service presented itself as a safe haven for various online cybercriminal activities, except for illicit content like child pornography, as stated by prosecutors in Florida. This platform reportedly facilitated the deployment of ransomware viruses by clients, which managed to infiltrate around 400 networks globally. Ransomware attacks commonly involve encrypting data on a victim organization’s computers, rendering them unusable until a ransom is paid.
The accused Polish citizen Grabowski and his alleged co-conspirators (5 were arrested) are said to have ignored law enforcement requests, shielded criminal elements from takedowns, and gained substantial profits from their service.
Grabowski is facing charges related to computer fraud, wire fraud, and conspiracy to commit international money laundering. Furthermore, a seizure order totaling $21.5 million has been issued against him.
The indictment against Grabowski was revealed in a Florida court on Wednesday, yet he currently remains at large.
According to the charging document, three other co-conspirators remain unindicted and unnamed in the scheme.
The “100% privacy hosting” service that Grabowski operated was seized by the IRS’ Criminal Investigation unit and the Federal Bureau of Investigation on Tuesday, August 8th. A citizen of Poland, Grabowski could face a maximum prison term of 45 years if he is apprehended and convicted.
Federal prosecutors have significantly escalated their efforts to counter ransomware attacks. Earlier this year, the Justice Department introduced a dedicated unit focused on combatting cyber threats to national security.
While numerous ransomware prosecutions have been disclosed in U.S. courts, the global dispersion of these perpetrators makes it uncertain how many will ultimately face incarceration.
According to the U.S. Court Documents:
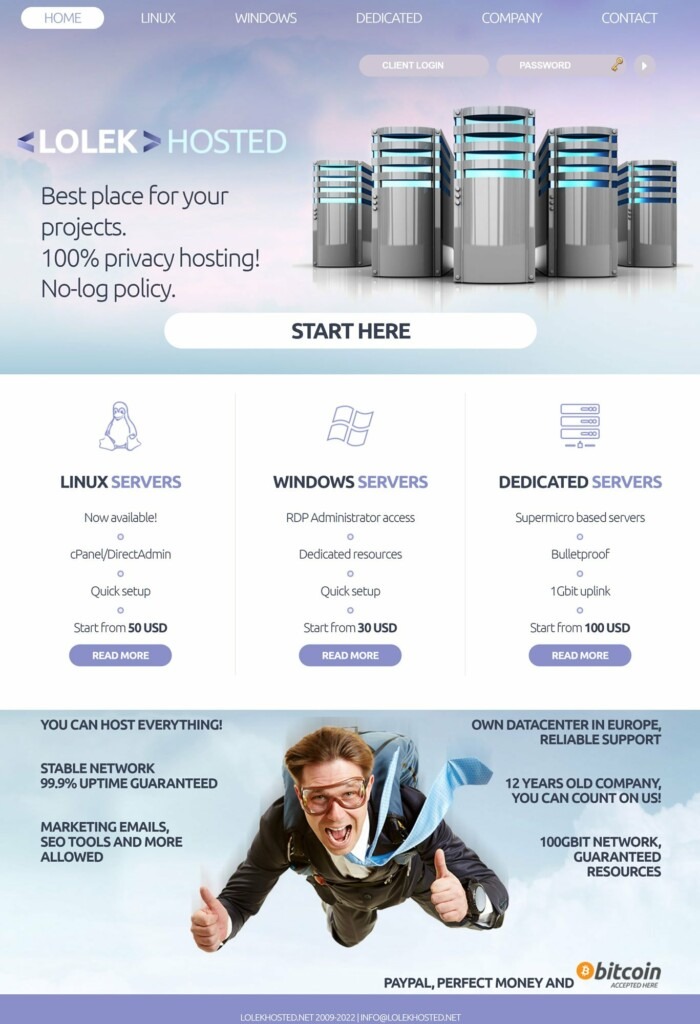
Artur Karol Grabowski, 36, operated a web hosting company named LolekHosted. Through LolekHosted, Grabowski provided “bulletproof” webhosting services, which is secure web hosting designed to facilitate malicious and criminal activities, including ransomware, brute-force attacks, and phishing. Grabowski allegedly facilitated the criminal activities of LolekHosted clients by allowing clients to register accounts using false information, not maintaining Internet Protocol (IP) address logs of client servers, frequently changing the IP addresses of client servers, ignoring abuse complaints made by third parties against clients, and notifying clients of legal inquiries received from law enforcement. Grabowski registered the domain “LolekHosted.net” in 2014, and advertised that its services were “bulletproof,” provided “100% privacy hosting,” and allowed clients to host “everything except child porn.”
The NetWalker ransomware was one of the ransomware variants facilitated by LolekHosted. The NetWalker ransomware was deployed on approximately 400 victim company networks, including municipalities, hospitals, law enforcement and emergency services, school districts, colleges, and universities, which resulted in the payment of more than 5,000 bitcoin in ransoms (currently valued at approximately $146 million). LolekHosted clients used its services to execute approximately 50 NetWalker ransomware attacks on victims located all over the world, including in the Middle District of Florida. Specifically, clients used the servers of LolekHosted as intermediaries when gaining unauthorized access to victim networks, and to store hacking tools and data stolen from victims.
On Aug. 8, U.S. authorities seized LolekHosted.net, the domain name LolekHosted used for nearly a decade. Visitors to LolekHosted.net will now find a seizure banner that notifies them that the domain name has been seized by federal authorities. The U.S. District Court for the Middle District of Florida issued the seizure warrant.
If convicted on all counts, Grabowski faces a maximum penalty of 45 years in prison. The indictment also notifies Grabowski that the United States is seeking an order of forfeiture in the amount of $21.5 million, the proceeds of the charged criminal conduct. Grabowski remains a fugitive.
Acting Assistant Attorney General Nicole M. Argentieri of the Justice Department’s Criminal Division and U.S. Attorney Roger B. Handberg for the Middle District of Florida made the announcement.
The FBI Tampa Field Office is investigating the case, with assistance from the IRS Criminal Investigation Cyber Crimes Unit.
Trial Attorney Sonia V. Jimenez of the Criminal Division’s Computer Crime and Intellectual Property Section and Assistant U.S. Attorneys Carlton C. Gammons and Suzanne Nebesky for the Middle District of Florida are prosecuting the case.
Substantial assistance was provided by the Justice Department’s Office of International Affairs and the FBI’s Legal Attaché Office in Warsaw, Poland. Polish authorities also provided substantial assistance.
According to Europol:
5 arrested in Poland for running bulletproof hosting service for cybercrime gangs
the Polish Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości) under the supervision of the Regional Prosecutor’s Office in Katowice (Prokuratura Regionalna w Katowicach) took action against LolekHosted.net, a bulletproof hosting service used by criminals to launch cyber-attacks across the world.
Five of its administrators were arrested, and all of its servers seized, rendering LolekHosted.net no longer available.
This latest success in the fight against cybercrime follows a complex investigation supported by Europol and the US Federal Bureau of Investigation (FBI).
Criminal hideouts for lease
Bulletproof hosting is a service in which an online infrastructure is offered, and operators will generally turn a blind eye to what customers use their rented domains for.
However, being willing to ignore the transgressions of clients does not mean that law enforcement will take the same stance.
The complex investigation into LolekHosted.net revealed how the service facilitated the distribution information-stealing malware, and also the launching of DDoS (distributed denial of service) attacks, fictitious online shops, Botnet server management and distribution of spam messages worldwide.
The suspects marketed privacy as a key feature of this service, using slogans such as “You can host anything here!” and “no-log policy”. Payments were to be made in cryptocurrencies.
European coordination
Europol’s European Cybercrime Centre (EC3) provided analytical support linking available data to various criminal cases within and outside the EU, and supported the investigation through operational analysis, crypto tracing, and forensic analysis.
The Joint Cybercrime Action Taskforce (J-CAT) hosted at Europol’s headquarters facilitated the information exchange. This standing operational team consists of cybercrime liaison officers from different countries who work on high-profile cybercrime investigations.
Resources:
- Sign up for SCARS professional support & recovery groups, visit support.AgainstScams.org
- Find competent trauma counselors or therapists, visit counseling.AgainstScams.org
- Become a SCARS Member and get free counseling benefits, visit membership.AgainstScams.org
- Report each and every crime, learn how to at reporting.AgainstScams.org
- Learn more about Scams & Scammers at RomanceScamsNOW.com and ScamsNOW.com
- Self-Help Books for Scam Victims are at shop.AgainsstScams.org
- Donate to SCARS and help us help others at donate.AgainstScams.org
More ScamsNOW.com Articles
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
SCARS LINKS: AgainstScams.org RomanceScamsNOW.com ContraEstafas.org ScammerPhotos.com Anyscam.com ScamsNOW.com
reporting.AgainstScams.org support.AgainstScams.org membership.AgainstScams.org donate.AgainstScams.org shop.AgainstScams.org
youtube.AgainstScams.org linkedin.AgainstScams.org facebook.AgainstScams.org
TABLE OF CONTENTS
CATEGORIES
![NavyLogo@4x-81[1] Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland](https://scamsnow.com/wp-content/uploads/2025/04/NavyLogo@4x-811.png)
ARTICLE META
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims.
- SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
- SCARS Institute now offers a free recovery learning program at www.SCARSeducation.org.
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery.
If you are looking for local trauma counselors, please visit counseling.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
Statement About Victim Blaming
Some of our articles discuss various aspects of victims. This is both about better understanding victims (the science of victimology) and their behaviors and psychology. This helps us to educate victims/survivors about why these crimes happened and not to blame themselves, better develop recovery programs, and help victims avoid scams in the future. At times, this may sound like blaming the victim, but it does not blame scam victims; we are simply explaining the hows and whys of the experience victims have.
These articles, about the Psychology of Scams or Victim Psychology – meaning that all humans have psychological or cognitive characteristics in common that can either be exploited or work against us – help us all to understand the unique challenges victims face before, during, and after scams, fraud, or cybercrimes. These sometimes talk about some of the vulnerabilities the scammers exploit. Victims rarely have control of them or are even aware of them, until something like a scam happens, and then they can learn how their mind works and how to overcome these mechanisms.
Articles like these help victims and others understand these processes and how to help prevent them from being exploited again or to help them recover more easily by understanding their post-scam behaviors. Learn more about the Psychology of Scams at www.ScamPsychology.org
SCARS INSTITUTE RESOURCES:
If You Have Been Victimized By A Scam Or Cybercrime
♦ If you are a victim of scams, go to www.ScamVictimsSupport.org for real knowledge and help
♦ SCARS Institute now offers its free, safe, and private Scam Survivor’s Support Community at www.SCARScommunity.org/register – this is not on a social media platform, it is our own safe & secure platform created by the SCARS Institute especially for scam victims & survivors.
♦ Enroll in SCARS Scam Survivor’s School now at www.SCARSeducation.org
♦ To report criminals, visit https://reporting.AgainstScams.org – we will NEVER give your data to money recovery companies like some do!
♦ Follow us and find our podcasts, webinars, and helpful videos on YouTube: https://www.youtube.com/@RomancescamsNowcom
♦ Learn about the Psychology of Scams at www.ScamPsychology.org
♦ Dig deeper into the reality of scams, fraud, and cybercrime at www.ScamsNOW.com and www.RomanceScamsNOW.com
♦ Scam Survivor’s Stories: www.ScamSurvivorStories.org
♦ For Scam Victim Advocates visit www.ScamVictimsAdvocates.org
♦ See more scammer photos on www.ScammerPhotos.com
You can also find the SCARS Institute’s knowledge and information on Facebook, Instagram, X, LinkedIn, and TruthSocial
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this and other SCARS articles are intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
Note about Mindfulness: Mindfulness practices have the potential to create psychological distress for some individuals. Please consult a mental health professional or experienced meditation instructor for guidance should you encounter difficulties.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here
If you are in crisis, feeling desperate, or in despair, please call 988 or your local crisis hotline – international numbers here.
More ScamsNOW.com Articles
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish. Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors’ experience. You can do Google searches, but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.
























![scars-institute[1] Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland](https://scamsnow.com/wp-content/uploads/2025/04/scars-institute1.png)

![niprc1.png1_-150×1501-1[1] Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland](https://scamsnow.com/wp-content/uploads/2025/04/niprc1.png1_-150x1501-11.webp)