Qakbot Botnet Infrastructure Shattered After An International Operation Led By FBI/Europol
By Europol, U.S. Department of Justice and SCARS Editorial Team – Society of Citizens Against Relationship Scams Inc.
Qakbot Malware Victimized 700 000+ Computers, With At Least EUR 54 Million Paid In Ransoms Since 2007
The Qakbot action represents the largest U.S./Europol-led financial and technical disruption of a botnet infrastructure
What is Qakbot Malware?
Qakbot is a ‘banking trojan’ type of virus or malware that has been around since 2007
It is a modular malware, which means that it can be customized to target specific victims or organizations. Qakbot is known for its ability to steal banking information, passwords, and other sensitive data. It can also be used to spread other malware, such as ransomware.
Qakbot is a dangerous malware because it can cause significant financial and reputational damage to victims. It can also be used to steal sensitive data, which can be used for identity theft or other crimes.
Qakbot is spread through a variety of ways, including:
- Phishing emails: Qakbot often spreads through phishing emails, which are emails that appear to be from a legitimate source, such as a bank or credit card company. The emails often contain a malicious attachment or link that, when clicked, installs Qakbot on the victim’s computer.
- Drive-by downloads: Qakbot can also be spread through drive-by downloads, which are downloads that occur automatically when a victim visits a malicious website.
- Exploit kits: Qakbot can also be spread through exploit kits, which are malicious software that exploits vulnerabilities in software to install Qakbot on a victim’s computer.
Cybercriminals used Qakbot to target critical infrastructure and businesses across multiple countries, stealing financial data & login credentials. Servers infected with Qakbot were detected by law enforcement in nearly 30 countries worldwide, enabling the malware’s activity on a global scale.
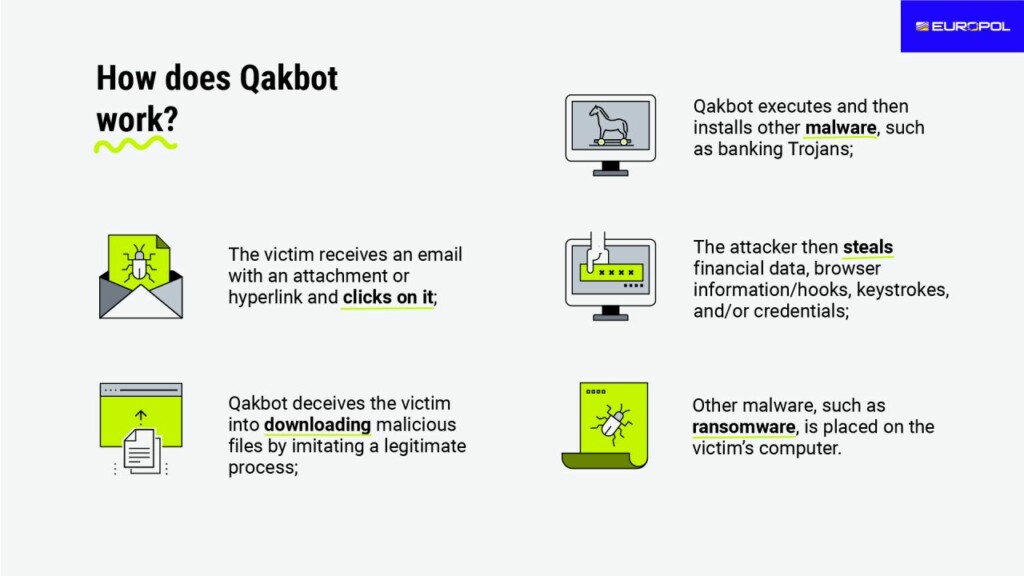
How does Qakbot work?
- The victim receives an email with an attachment or hyperlink and clicks on it;
- Qakbot deceives the victim into downloading malicious files by imitating a legitimate process;
- Qakbot executes and then installs other malware, such as banking Trojans;
- The attacker then steals financial data, browser information/hooks, keystrokes, and/or credentials;
- Other malware, such as ransomware, is placed on the victim’s computer.
The Qakbot Operation
The investigation, supported by Europol and Eurojust, involved judicial & law enforcement authorities from France, Germany, Latvia, The Netherlands, Romania, the United Kingdom, and the United States.
According to Europol:
Europol has supported the coordination of a large-scale international operation that has taken down the infrastructure of the Qakbot malware and led to the seizure of nearly EUR 8 million in cryptocurrencies. The international investigation, also supported by Eurojust, involved judicial and law enforcement authorities from France, Germany, Latvia, The Netherlands, Romania, the United Kingdom, and the United States. Qakbot, operated by a group of organized cybercriminals, targeted critical infrastructure and businesses across multiple countries, stealing financial data and login credentials. Cybercriminals used this persistent malware to commit ransomware, fraud, and other cyber-enabled crimes.
Active since 2007, this prolific malware (also known as QBot or Pinkslipbot) evolved over time using different techniques to infect users and compromise systems. Qakbot infiltrated victims’ computers through spam emails containing malicious attachments or hyperlinks. Once installed on the targeted computer, the malware allowed for infections with next-stage payloads such as ransomware. Additionally, the infected computer became part of a botnet (a network of compromised computers) controlled simultaneously by the cybercriminals, usually without the knowledge of the victims. However, Qakbot’s primary focus was on stealing financial data and login credentials from web browsers.
Over 700 000 infected computers worldwide
According to Europol:
A number of ransomware groups used Qakbot to carry out a large number of ransomware attacks on critical infrastructure and businesses. The administrators of the botnet provided these groups with access to the infected networks for a fee. The investigation suggests that between October 2021 and April 2023, the administrators received fees corresponding to nearly EUR 54 million in ransoms paid by the victims. The lawful examination of the seized infrastructure uncovered that the malware had infected over 700,000 computers worldwide. Law enforcement detected servers infected with Qakbot in almost 30 countries in Europe, South and North America, Asia, and Africa, enabling the malware’s activity on a global scale.
Over the course of the investigation, Europol facilitated the information exchange between participating agencies, supported the coordination of operational activities, and funded operational meetings. Europol also provided analytical support linking available data to various criminal cases within and outside the EU. The Joint Cybercrime Action Taskforce (J-CAT) at Europol also supported the operation. This standing operational team consists of cybercrime liaison officers from different countries who work on high-profile cybercrime investigations.
Eurojust actively facilitated the cross-border judicial cooperation between the national authorities involved. The Agency hosted a coordination meeting in July 2023 to facilitate evidence sharing and to prepare for this joint operation.
The U.S. Department of Justice’s Role
According to the U.S. Department of Justice
Qakbot Malware Disrupted in International Cyber Takedown
Qakbot Malware Infected More Than 700,000 Victim Computers, Facilitated Ransomware Deployments, and Caused Hundreds of Millions of Dollars in Damage
LOS ANGELES – The Justice Department today announced a multinational operation involving actions in the United States, France, Germany, the Netherlands, the United Kingdom, Romania, and Latvia to disrupt the botnet and malware known as Qakbot and take down its infrastructure.
The Qakbot malicious code is being deleted from victim computers, preventing it from doing any more harm. The Department also announced the seizure of more than $8.6 million in cryptocurrency in illicit profits.
The action represents the largest U.S.-led financial and technical disruption of a botnet infrastructure leveraged by cybercriminals to commit ransomware, financial fraud, and other cyber-enabled criminal activity.
“Cybercriminals who rely on malware like Qakbot to steal private data from innocent victims have been reminded today that they do not operate outside the bounds of the law,” said Attorney General Merrick B. Garland. “Together with our international partners, the Justice Department has hacked Qakbot’s infrastructure, launched an aggressive campaign to uninstall the malware from victim computers in the United States and around the world, and seized $8.6 million in extorted funds.”
“An international partnership led by the Justice Department and the FBI has resulted in the dismantling of Qakbot, one of the most notorious botnets ever, responsible for massive losses to victims around the world,” said United States Attorney Martin Estrada. “Qakbot was the botnet of choice for some of the most infamous ransomware gangs, but we have now taken it out. This operation also has led to the seizure of almost 9 million dollars in cryptocurrency from the Qakbot cybercriminal organization, which will now be made available to victims. My Office’s focus is on protecting and vindicating the rights of victims, and this multifaceted attack on computer-enabled crime demonstrates our commitment to safeguarding our nation from harm.”
“The Operation ‘Duck Hunt’ Team utilized their expertise in science and technology, but also relied on their ingenuity and passion to identify and cripple Qakbot, a highly structured and multi-layered bot network that was literally feeding the global cybercrime supply chain,” said Donald Alway, the Assistant Director in Charge of the FBI’s Los Angeles Field Office. “These actions will prevent an untold number of cyberattacks at all levels, from the compromised personal computer to a catastrophic attack on our critical infrastructure.”
According to court documents, Qakbot, also known by various other names, including “Qbot” and “Pinkslipbot,” is controlled by a cybercriminal organization and used to target critical industries worldwide. The Qakbot malware primarily infects victim computers through spam email messages containing malicious attachments or hyperlinks. Once it has infected a victim computer, Qakbot can deliver additional malware, including ransomware, to the infected computer. Qakbot has been used as an initial means of infection by many prolific ransomware groups in recent years, including Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta. The ransomware actors then extort their victims, seeking ransom payments in bitcoin before returning access to the victim computer networks.
These ransomware groups caused significant harm to businesses, healthcare providers, and government agencies all over the world, including to a power engineering firm based in Illinois; financial services organizations based in Alabama, Kansas, and Maryland; a defense manufacturer based in Maryland; and a food distribution company in Southern California. Investigators have found evidence that, between October 2021 and April 2023, Qakbot administrators received fees corresponding to approximately $58 million in ransoms paid by victims.
The victim computers infected with Qakbot malware are part of a botnet (a network of compromised computers), meaning the perpetrators can remotely control all the infected computers in a coordinated manner. The owners and operators of the victim computers are typically unaware of the infection.
As part of the takedown, the FBI was able to gain access to Qakbot infrastructure and identify over 700,000 computers worldwide, including more than 200,000 in the United States, that appear to have been infected with Qakbot. To disrupt the botnet, the FBI was able to redirect Qakbot botnet traffic to and through servers controlled by the FBI, which in turn instructed infected computers in the United States and elsewhere to download a file created by law enforcement that would uninstall the Qakbot malware. This uninstaller was designed to untether the victim computer from the Qakbot botnet, preventing further installation of malware through Qakbot.
The scope of this law enforcement action was limited to information installed on the victim computers by the Qakbot actors. It did not extend to remediating other malware already installed on the victim computers and did not involve access to or modification of the information of the owners and users of the infected computers.
Valuable technical assistance was provided by Zscaler. The FBI has partnered with the Cybersecurity and Infrastructure Security Agency, Shadowserver, Microsoft Digital Crimes Unit, the National Cyber Forensics and Training Alliance, and Have I Been Pwned to aid in victim notification and remediation.
The FBI Los Angeles Field Office, the U.S. Attorney’s Office for the Central District of California, and the Criminal Division’s Computer Crime and Intellectual Property Section (CCIPS) conducted the operation in close cooperation with Eurojust. Investigators and prosecutors from several jurisdictions provided crucial assistance, including Europol, French Police Cybercrime Central Bureau and the Cybercrime Section of the Paris Prosecution Office, Germany’s Federal Criminal Police and General Public Prosecutor’s Office Frankfurt/Main, Netherlands National Police and National Public Prosecution Office, the United Kingdom’s National Crime Agency, Romania’s National Police, and Latvia’s State Police. The Justice Department’s Office of International Affairs and the FBI Milwaukee Field Office provided significant assistance.
Significance of the Qakbot Takedown!
The importance of the Europol takedown of the Qakbot malware takedown this week for cybersecurity and the public is significant.
Qakbot is a modular banking trojan virus/malware that has been around since 2007 and is known for its ability to steal banking information, passwords, and other sensitive data. It can also be used to spread other malware, such as ransomware.
The takedown of Qakbot is a major victory for cybersecurity, as it will make it more difficult for criminals to use this malware to steal from victims. It is also a positive development for the public, as it will help to protect people from becoming victims of financial fraud and identity theft.
The takedown of Qakbot was a coordinated effort by Europol and FBI, and other law enforcement agencies from the United Kingdom, France, Germany, the Netherlands, Romania, and Latvia. The agencies worked together to identify and disrupt the infrastructure that was being used to distribute Qakbot.
The takedown of Qakbot is a reminder that law enforcement agencies are working to combat cybercrime and that they are making progress. However, it is important to remember that cybercrime is a constantly evolving threat and that criminals will always be looking for new ways to exploit vulnerabilities.
Law enforcement authorities involved:
- France: National Police (Police Nationale) and National Gendarmerie (Gendarmerie Nationale)
- Germany: Federal Criminal Police Office (Bundeskriminalamt)
- Latvia: State Police (Valsts policija)
- The Netherlands: National Police (Politie)
- Romania: Romanian Police (Poliția Română)
- United Kingdom: National Crime Agency
- United States: Federal Bureau of Investigation (US FBI)
Judicial authorities involved:
- France: National Jurisdiction against Organised Crime (JUNALCO), Public Prosecutor’s Office Cybercrime Unit;
- Germany: Prosecutor General’s Office Frankfurt am Main – Cyber Crime Centre;
- The Netherlands: National Public Prosecutor’s Office Rotterdam
- United States: US Attorney’s Office for the Central District of California and the Department of Justice’s Computer Crime and Intellectual Property Section
SCARS Resources:
- For New Victims of Relationship Scams newvictim.AgainstScams.org
- Subscribe to SCARS Newsletter newsletter.againstscams.org
- Sign up for SCARS professional support & recovery groups, visit support.AgainstScams.org
- Find competent trauma counselors or therapists, visit counseling.AgainstScams.org
- Become a SCARS Member and get free counseling benefits, visit membership.AgainstScams.org
- Report each and every crime, learn how to at reporting.AgainstScams.org
- Learn more about Scams & Scammers at RomanceScamsNOW.com and ScamsNOW.com
- Global Cyber Alliance ACT Cybersecurity Tool Website: Actionable Cybersecurity Tools (ACT) (globalcyberalliance.org)
- Self-Help Books for Scam Victims are at shop.AgainstScams.org
- Donate to SCARS and help us help others at donate.AgainstScams.org
- Worldwide Crisis Hotlines: International Suicide Hotlines – OpenCounseling : OpenCounseling
- Campaign To End Scam Victim Blaming – 2024 (scamsnow.com)
More:
- Cybercrime/Cybersecurity Training Has Failed! (scamsnow.com)
- The Cost Of Global Cybercrime (scamsnow.com)
- The Subtle Sabotage Of Blame In Cybersecurity & Online Safety (scamsnow.com)
- Organisations Telling Users To ‘Avoid Clicking Bad Links’ Still Isn’t Working (scamsnow.com)
- Cybersecurity Failure Is Inevitable – Plan For It (scamsnow.com)
- EncroChat Dismantling Led To Over 6,500 Arrests (scamsnow.com)
- Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland (scamsnow.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
More ScamsNOW.com Articles
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment above!
SCARS LINKS: AgainstScams.org RomanceScamsNOW.com ContraEstafas.org ScammerPhotos.com Anyscam.com ScamsNOW.com
reporting.AgainstScams.org support.AgainstScams.org membership.AgainstScams.org donate.AgainstScams.org shop.AgainstScams.org
youtube.AgainstScams.org linkedin.AgainstScams.org facebook.AgainstScams.org
ARTICLE RATING
TABLE OF CONTENTS
- Qakbot Botnet Infrastructure Shattered After An International Operation Led By FBI/Europol
- Qakbot Malware Victimized 700 000+ Computers, With At Least EUR 54 Million Paid In Ransoms Since 2007
- What is Qakbot Malware?
- How does Qakbot work?
- The Qakbot Operation
- Over 700 000 infected computers worldwide
- The U.S. Department of Justice’s Role
- Significance of the Qakbot Takedown!
- Law enforcement authorities involved:
- Judicial authorities involved:
- SCARS Resources:
- More:
- Important Information for New Scam Victims
- Statement About Victim Blaming
- SCARS INSTITUTE RESOURCES:
- Psychology Disclaimer:
- More ScamsNOW.com Articles
- A Question of Trust
- SCARS Institute™ ScamsNOW Magazine
Society of Citizens Against Relationship Scams Inc. [SCARS]
META
CATEGORIES
MOST POPULAR COMMENTED ARTICLES
POPULAR ARTICLES
U.S. & Canada Suicide Lifeline 988
![NavyLogo@4x-81[1]](https://scamsnow.com/wp-content/uploads/2025/04/NavyLogo@4x-811.png)
WHAT PEOPLE ARE TALKING ABOUT
LATEST SITE COMMENTS
See Comments for this Article at the Bottom of the Page
on Vulnerability to Scams Caused by Past Relationships is Like a River Running through Your Life Cutting Channels – 2025: “My big take away from this article is that there are many layers to my vulnerability. Yes, losing my Mom…” May 8, 11:43
on Hate for Scammers and Criminals Feels So Good But is So Bad for Scam Victims – 2025: “As stated here it feels like it should be justified – to hate them. I never did feel that way,…” May 6, 17:32
on Scam Victims Suppressing Trauma Or Avoiding Recovery And Healing 2024: “This is a great article that will, hopefully, help when I am avoiding facing my emotions/triggers. Recognizing the signs and…” May 6, 16:47
on SCARS 5 Coping Techniques For Traumatized Scam Victims – 2023: “One of the best ways of coping for me has been to reconnect with my friends. I self-isolated for months…” May 6, 16:07
on Trauma Recollection/Traumatic Flashbacks And Scam Victim PTSD – Recovery Psychology – 2023: “I don’t feel like my trauma can be described as PTSD. The affects after the scam ended were severe anxiety,…” May 6, 15:55
on Selective Amnesia and Scam Victim Psychological Trauma 2023: “This was a very interesting article to me. I have not experienced selective amnesia in relation to the scam. However,…” May 6, 15:39
on Psychological Triggers/Emotional Triggers – What They Are And How They Work – 2023/2024: “Not long after my scam ended, I needed to go to the grocery store. It never crossed my mind that…” May 6, 14:48
on Learning And The Challenges That A Scam Victim Faces From Trauma And Related Cognitive Effects – 2024: “My cognitive impairment was bad right after my scam. However, I have now noticed that it was especially bad during…” May 6, 14:23
on Hate for Scammers and Criminals Feels So Good But is So Bad for Scam Victims – 2025: “This is all true and valid. I had to forgive myself first for trusting my abuser because he hurt my…” May 6, 10:08
on Nirvana and the Path to Letting Go of Suffering – 2025: “En mi experiencia podría describir el nirvana en mi recuperación como ese estado de paz profunda y liberación emocional que…” May 5, 18:58
on The Prodigal Son or Daughter – Returning ‘Home’ After the Scam – 2025: “It’s true that the judgment of others does not define my path but if after “coming home” those closest to…” May 5, 13:21
on Beginning Again and Scam Victim Recovery -2025: “Taking action is the first step to recovery and I am doing that and becoming a newer stronger version of…” May 5, 09:53
on Beginning Again and Scam Victim Recovery -2025: “In order not to let this deception define me, since its discovery I have been ACTING.” May 5, 07:22
on The Butterfly Effect And Scam Victims – 2024: “Very good and interesting analogy to the Butterfly Effect and how it pertains to scams. In my crime I can…” May 4, 14:51
on Faith And Why It Matters In Scam Victim Recovery – 2024: “This is a good article giving examples of the difference between faith in oneself and one’s core values – to…” May 4, 13:37
on Reclaiming Your Worth: A Scam Survivor’s Guide to Navigating Your Worthiness After a Scam – 2023: “As an individual I process my emotions slowly whether it is shock, trauma, anger, disbelief. In the cycle of recovery…” May 4, 12:54
on The Stain that Never Goes Away After a Romance Scam for Scam Victims – 2025: “Thank you for sharing this important step on recovery” May 4, 12:09
on Metanoia – The Transformation for Traumatized Scam Victims – 2025: “Excelente articulo!!!… Después de superar la estafa podría describir la metanoia en mi propia experiancia como un renacimiento interior, una…” May 4, 00:24
on Philosophy of Life Planning – From Chaos to Order and the Scam Victim Recovery Path Forward – 2025: “Seeking justice is, unfortunately, not justice. Anger and revenge is not justice either. Recovery is justice. The only justice for…” May 3, 21:16
Important Information for New Scam Victims
Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims
SCARS Institute now offers a free recovery program at www.SCARSeducation.org
Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery
If you are looking for local trauma counselors, please visit counseling.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
Statement About Victim Blaming
Some of our articles discuss various aspects of victims. This is both about better understanding victims (the science of victimology) and their behaviors and psychology. This helps us to educate victims/survivors about why these crimes happened and not to blame themselves, better develop recovery programs, and help victims avoid scams in the future. At times, this may sound like blaming the victim, but it does not blame scam victims; we are simply explaining the hows and whys of the experience victims have.
These articles, about the Psychology of Scams or Victim Psychology – meaning that all humans have psychological or cognitive characteristics in common that can either be exploited or work against us – help us all to understand the unique challenges victims face before, during, and after scams, fraud, or cybercrimes. These sometimes talk about some of the vulnerabilities the scammers exploit. Victims rarely have control of them or are even aware of them, until something like a scam happens, and then they can learn how their mind works and how to overcome these mechanisms.
Articles like these help victims and others understand these processes and how to help prevent them from being exploited again or to help them recover more easily by understanding their post-scam behaviors. Learn more about the Psychology of Scams at www.ScamPsychology.org
SCARS INSTITUTE RESOURCES:
IF YOU HAVE BEEN VICTIMIZED BY A SCAM OR CYBERCRIME
♦ If you are a victim of scams, go to www.ScamVictimsSupport.org for real knowledge and help
♦ Enroll in SCARS Scam Survivor’s School now at www.SCARSeducation.org
♦ To report criminals, visit https://reporting.AgainstScams.org – we will NEVER give your data to money recovery companies like some do!
♦ Sign up for our free support & recovery help by https://support.AgainstScams.org
♦ Join our WhatsApp Chat Group at: https://chat.whatsapp.com/BPDSYlkdHBbDBg8gfTGb02
♦ Follow us on X: https://x.com/RomanceScamsNow
♦ Follow us and find our podcasts, webinars, and helpful videos on YouTube: https://www.youtube.com/@RomancescamsNowcom
♦ SCARS Institute Songs for Victim-Survivors: https://www.youtube.com/playlist…
♦ See SCARS Institute Scam Victim Self-Help Books at https://shop.AgainstScams.org
♦ Learn about the Psychology of Scams at www.ScamPsychology.org
♦ Dig deeper into the reality of scams, fraud, and cybercrime at www.ScamsNOW.com and www.RomanceScamsNOW.com
♦ Scam Survivor’s Stories: www.ScamSurvivorStories.org
♦ For Scam Victim Advocates visit www.ScamVictimsAdvocates.org
♦ See more scammer photos on www.ScammerPhotos.com
You can also find the SCARS Institute on Facebook, Instagram, X, LinkedIn, and TruthSocial
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this and other SCARS articles are intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
Note about Mindfulness: Mindfulness practices have the potential to create psychological distress for some individuals. Please consult a mental health professional or experienced meditation instructor for guidance should you encounter difficulties.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here
If you are in crisis, feeling desperate, or in despair, please call 988 or your local crisis hotline.
More ScamsNOW.com Articles
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish. Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors’ experience. You can do Google searches, but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.














![scars-institute[1]](https://scamsnow.com/wp-content/uploads/2025/04/scars-institute1.png)
![niprc1.png1_-150×1501-1[1]](https://scamsnow.com/wp-content/uploads/2025/04/niprc1.png1_-150x1501-11.webp)
